From Supervision to "Superveillance"
Risk Mitigation for Electronic Communications
One of the most important topics raised at our recent Innovation Exchange Conference on “The Future of Work in Financial Services” is how risk mitigation intersects with technology innovation. Individuals within firms that look at risk mitigation through the lens of lexicon-based methods of supervisory review are deeply familiar with the strengths and limitations of these methods in enforcing their written supervisory procedures (WSPs).
Conversely, those focused on advanced, machine-driven methods of content surveillance and inspection understand the challenges of building effective models against increasingly heterogeneous datasets and interactive content sources. These dueling perspectives raise several questions, including:
- What is the difference between supervision and surveillance?
- Are lexicons and models fundamentally at odds with one another?
- Can supervisory and surveillance processes co-exist or, ideally, feed one another?
We tackled these questions in our session “From Supervision to Surveillance,” with experts Shaun Hurst, Gregory Breeze, and our new colleague from Digital Reasoning, Svetlana Godjevac. I’ll share some of their insights below.
As we ask these questions, we continue to see responses all over the map. We frequently join a meeting to discuss “surveillance” initiatives, only to find that most requirements pertain directly to supervisory review. We’ve also seen many technologies that are well-suited for “surveillance” but lack capabilities to address compliant capture, storage, and policy management. So, let’s first attempt to calibrate with some basic definitions.
Electronic communications supervision versus surveillance
Traditionally, supervisory review, or supervision, has referred to the review of communications of registered representatives to meet requirements in FINRA 3110 and elsewhere. Basically, a review of content to determine who has communicated with whom about what. Many firms have designed review processes to evaluate email using keyword-based lexicons. These are assembled into policies, based upon existing supervisory workflows, to determine the appropriate escalation and action for potential policy violations. These systems are designed to address known policy infractions, as opposed to those that may be disguised by those attempting to evade compliance scrutiny.
In contrast, surveillance has traditionally focused on the analysis of activity. It often uses natural language processing or machine learning to identify anomalies without pre-defined rules. It has also undergone a surge of interest due to regulations such as MiFID II (which requires that all communications be captured, inspected, and married against a transactional event), as well as firms converging upon shared views of information risk across legal, compliance, and security departments as they deal with today’s distributed workforces.
Fortunately, the needs for supervision and surveillance are not mutually exclusive. In fact, business requirements are often a mix of both, with policy violations representing a continuum versus discrete endpoints, as illustrated here:
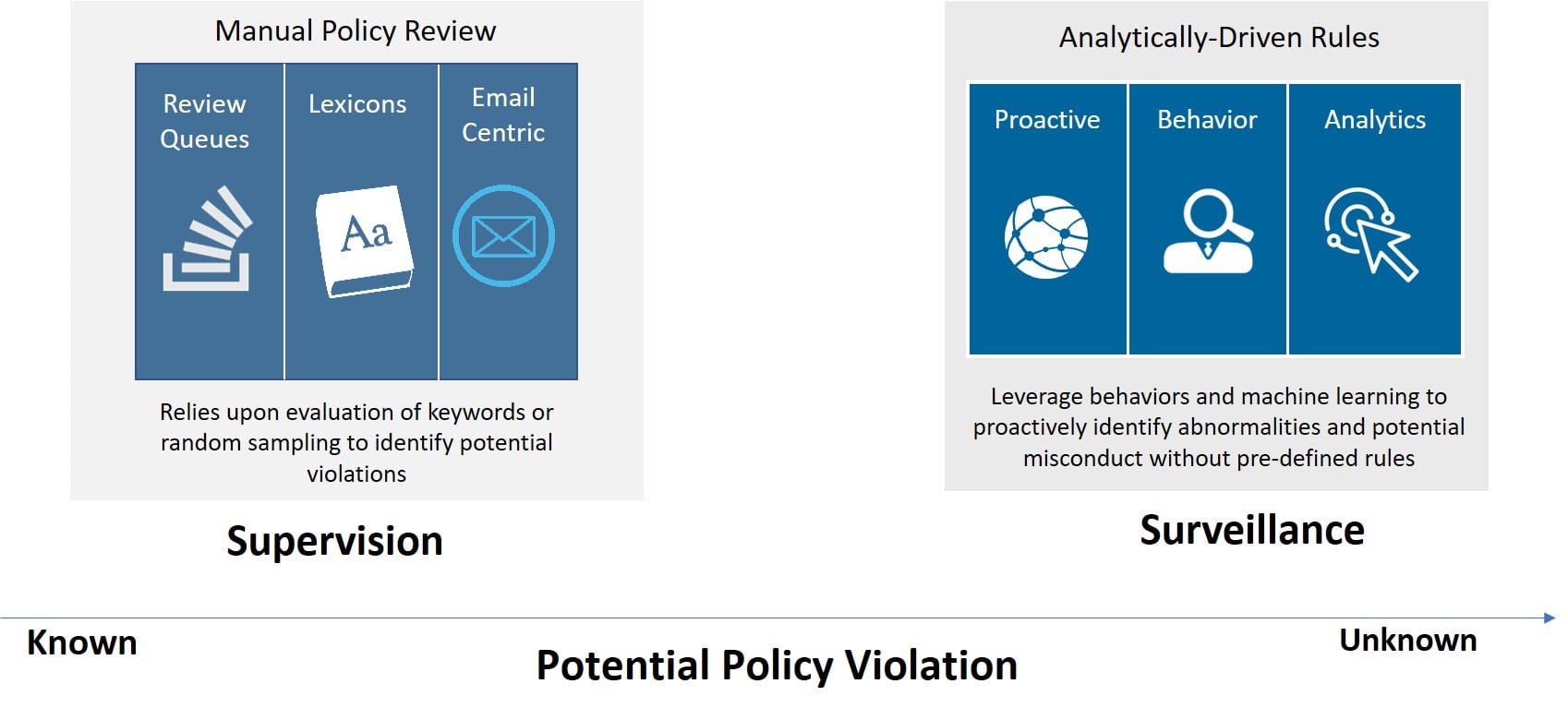
Consequently, firms that have a mix of requirements should look for solutions that help to improve the efficiency of established supervisory processes while providing the analytics to uncover the previously unknown categories of policy violations.
How supervisory and surveillance solutions can co-exist
As more firms seek solutions that address both supervision and surveillance requirements, firms should keep a few principles in mind: they must cover the compliance fundamentals as well as yielding new insights with analytics; they must address all communication sources in use by representatives; and they must be open and extensible to fit into the compliance, supervisory, and investigative fabric within an organization.
In describing the intersection of supervision and surveillance, we’d like to offer the following as a definition to address these requirements:
Holistic insight into conduct across activities and communications channels, using a continuous feedback loop of pre-defined rules (supervision) and identification of anomalous behavior (surveillance).
Coined “superveillance” by my colleague Greg Breeze, this intersection can be expressed visually as delivering capabilities that cover the spectrum — from the known, regulatory-driven supervisory requirements to the unknown and hidden risks that are uncovered through the use of advanced analytics. It encompasses the compliance fundamentals of policy management and storage, as well as the ability to use behavioral and sentiment analysis to uncover actions of high-risk brokers requiring heightened supervision.
Importantly, the outcomes in uncovering unknown risks should be fed back to build into new policies and rules for use in future supervisory tasks. Superveillance should also treat each content source natively, so the breadth of email, social media, unified communications and other sources can be normalized and delivered to external systems for trade reconciliation.
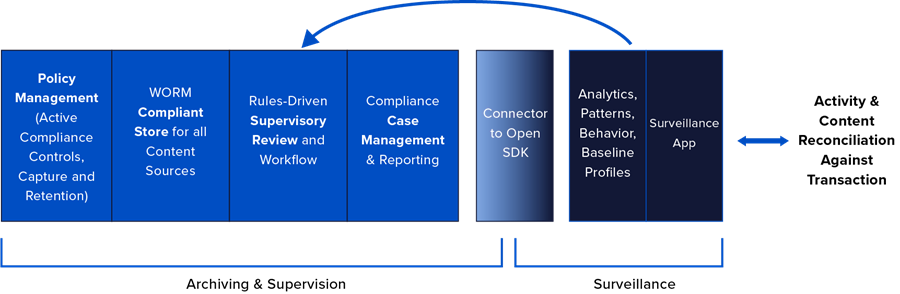
Defining the ideal “superveillance” solution attributes
Given the number of specialized technology domains touched by superveillance, don’t expect a "one-size-fits-all" solution. Many firms have already invested in specific components and are more concerned about how new technologies will interoperate or feed those existing solutions. Superveillance should be a critical element of the risk management fabric within an organization and, accordingly, firms should be prioritizing the following attributes when evaluating solutions:
Openness and extensibility: Superveillance requires the ability to deliver content downstream and return insights back upstream to further inform policies. Doing so requires fully accessible APIs, connectors, and SDKs to address custom content sources. The benefits of leveraging cloud technologies are greatly diminished when utilizing technology that cannot communicate or collaborate with other vital systems.
Ability to preserve all content sources: firms today are using a multitude of communications sources, each of which must be captured and preserved to meet regulatory mandates. Modern superveillance solutions will handle each of those sources natively, with conversations preserved for more efficient review and analysis — unlike legacy supervisory tools that convert non-email sources into an email format.
Coverage for the compliance fundamentals: solutions touching superveillance processes must be purpose-built for compliance and ensure that content is captured with the appropriate chain-of-custody, immutable storage, and policy management capabilities required by any SEC, FINRA, or MiFID II regulated firm. Superveillance extends the boundaries of traditional supervisory review — it does not replace or diminish the importance of managing day-to-day tasks more efficiently or effectively.
Scale and performance: given the large volume of transactions requiring reconciliation and the overwhelming volume of communications data in general, superveillance solutions must be designed for enterprise scale. They should not restrict the use of analytics to defined data subsets applying only to registered representatives. Today’s information risks can reside anywhere. The ability to broaden the supervisory lens to cover all corners and edges of the risk perimeter is paramount
Security and privacy by design: clearly, superveillance solutions will touch some of the most sensitive and important assets governed by a firm. Any solution designed for use in today’s world of increasingly complex security threats and evolving data privacy mandates must provide the audited protocols, third-party attestations, and in-house expertise to reveal and respond to any risk exposed in its everyday use. As we see across the industry — compliance must work in harmony with other functions to create a more effective response to today’s information risks.
Where to go from here
Given the significant differences between traditional supervisory and surveillance tools, a good place to start is your vocabulary and definitions to ensure you’re speaking the same language as your vendor. Once nomenclature is established, firms can explore whether traditional capabilities are equipped to address their current communications patterns and today’s information risks — or whether defining the requirements for a superveillance solution is the better path toward a holistic approach to achieving insights across activities and communications networks.
Share this post!
Smarsh Blog
Our internal subject matter experts and our network of external industry experts are featured with insights into the technology and industry trends that affect your electronic communications compliance initiatives. Sign up to benefit from their deep understanding, tips and best practices regarding how your company can manage compliance risk while unlocking the business value of your communications data.





Subscribe to the Smarsh Blog Digest
Subscribe to receive a monthly digest of articles exploring regulatory updates, news, trends and best practices in electronic communications capture and archiving.
Smarsh handles information you submit to Smarsh in accordance with its Privacy Policy. By clicking "submit", you consent to Smarsh processing your information and storing it in accordance with the Privacy Policy and agree to receive communications from Smarsh and its third-party partners regarding products and services that may be of interest to you. You may withdraw your consent at any time by emailing privacy@smarsh.com.
FOLLOW US